Cloudockit Compliance Features & AWS, Azure, GCP Built-in Security Features
Controlling and monitoring your cloud environments is vital to secure your data. In this article, we will compare the tools to monitor and control your cloud environments for Azure, AWS and Google Cloud Platform. Additionally, learn how Cloudockit can help you ensure your environments are conform with your plans.
Build-in Security Features For Your Cloud Providers
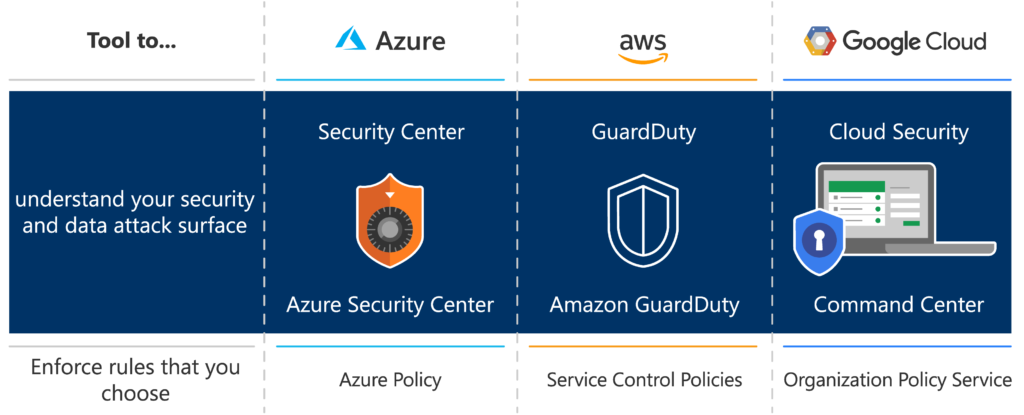
Microsoft Azure
- Azure provides a security center that will give you insight on potential issues regarding security. You can see more about Security Center here: Azure Security.
- Azure gives you the ability to create “Azure Policies”. The policies are a way to ensure that only your defined and confirmed rules are deployed. For example, you can create a policy that prevents deploying something outside East-US Location. You can find more information at Azure Policy.
Amazon Web Services
- AWS provides a feature called GuardDuty. The feature’s objective is to allow threat detection and monitor for unauthorized behavior. It works by analyzing your CloudTrail Events, VPC flow logs, DNS Logs and interpreting them to find abnormalities. You can find more information by visiting AWS GuardDuty.
- Service Control Policies, which stands on top of permissions, will allow you to control what users can do. For example, you can create a policy that will prevent users from disabling AWS CloudTrail. You can see more at AWS’s User Guide.
Google Cloud Platform
- GCO Organization Policy services will allow you to control compliance across your entire resource hierarchy. Within a policy, you will be able to define a constraint that will be enforced. For example, you can create a policy with a constraint ‘Disable VM Nested Virtualization’ to ensure none of the Virtual Machines in your GCP environment has Virtual Machines running inside. You can see more about GCP Organization Policy here: Organization Policy Service
- Cloud Security Command Center (Cloud SCC) does Anomaly Detection by detecting potential account hijacking and also gives you the ability to display a list of all the assets you have in your GCP project with a list of warnings for each of these assets.
Lear how Cloudockit can increase security of your cloud
Benefits of Cloudockit’s Compliance Rules Engine
Cloudockit’s Compliance Rule features allows you control but stay agile instead of blocking and preventing users from working in the cloud. With Cloudockit, you will have the ability to create advanced rules yourself instead of being constraint to Azure, AWS or GCP limited rules. In addition, you will be able to make all your changes in Cloudockit’s Graphical User Interface (GUI) instead of having to manipulate JSON files.
Finally, Cloudockit is a true Multi-Cloud Management tool, therefore you will not have to define rules individually for each cloud provider.
Features of Cloudockit’s Compliance Rules Engine
Let’s have a look at the different options that we offer with the compliance rules in Cloudockit.
Compliance Tab
You can access this section clicking on the Compliance Tab
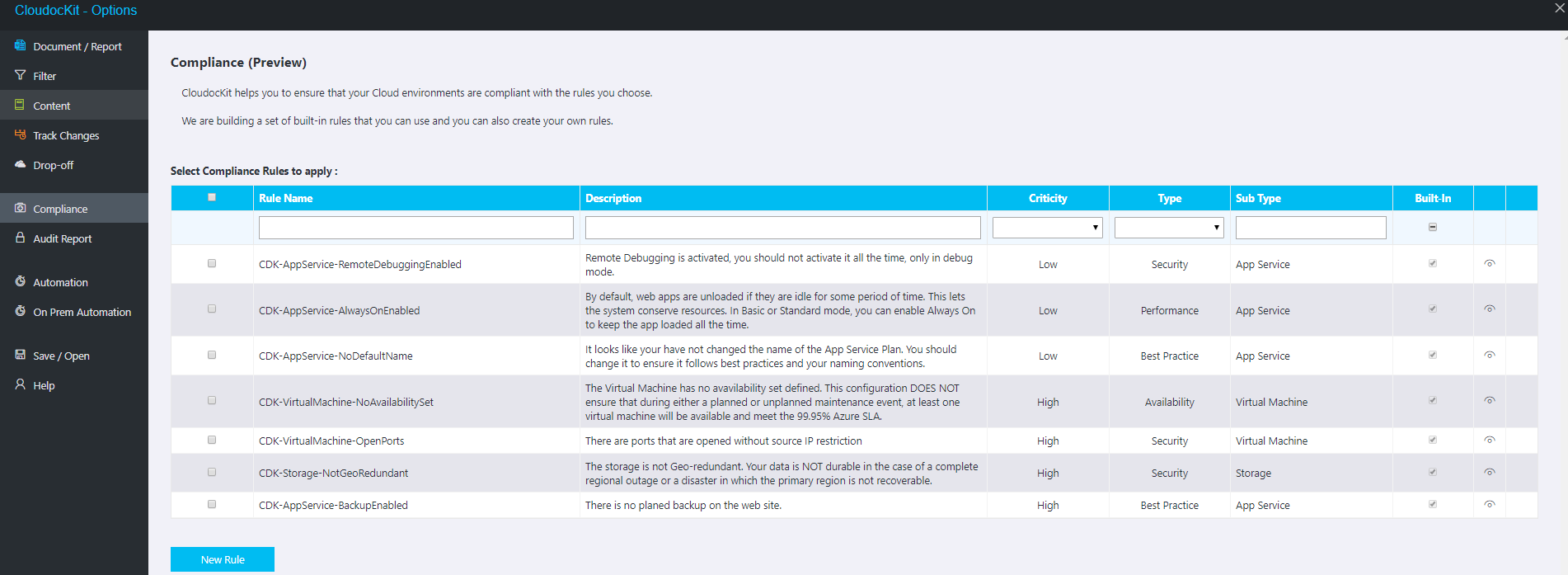
As you can see, there are some built-in rules. Click on one of them to see how it is structured:
I am text block. Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Cloudockit Buit-in Rules Preview
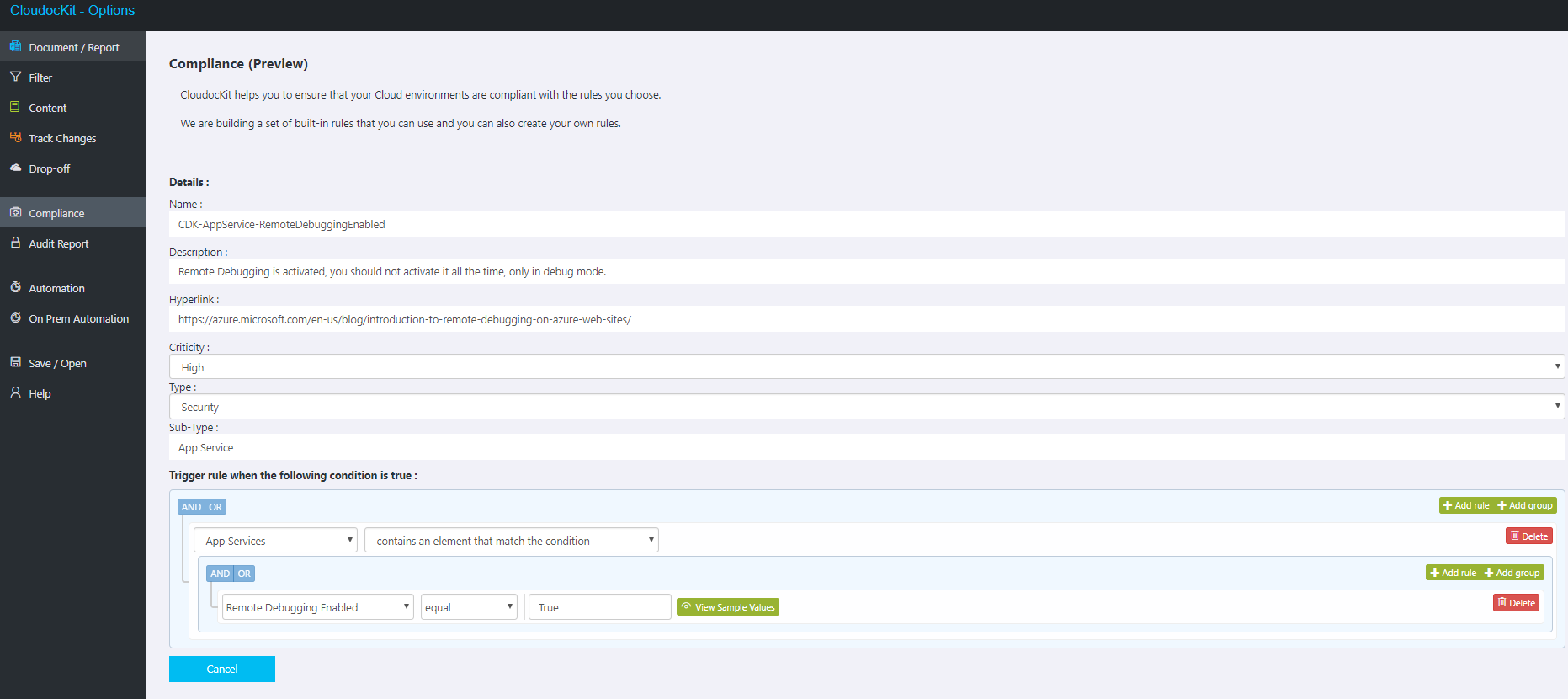
A Compliance Rule is mainly compound of two parts:
- Information about the rule classification (Name, Description, Link, Type, etc)
- Trigger about when the Compliance Rule is true
In the previous, screenshot, the rule CDK-AppService-RemoteDebuggingEnabled objective is to ensure that App Services do not have Remote Debugging Activated.
The trigger is as follow:
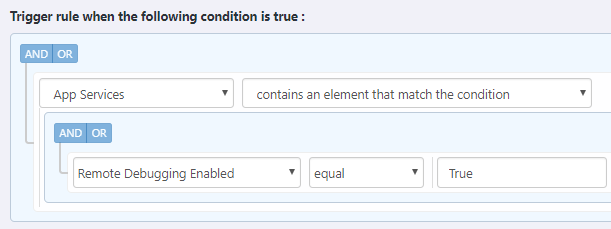
With this rule, you want to ensure that no Virtual Machine should contain a NIC that has an NSG that contains a rule whose address prefix is *. Notice that you can build even more complex rules by using Group and AND/OR Conditions.
These rules are available to AWS, GCP and Azure so you do not need to learn multiple syntaxes.
Additionally, Cloudockit will gives you the warnings that you want but it will also automatically generate your Azure, AWS and Google Cloud Platform Documentation & Diagrams to ensure your environment is compliant. Indeed, compliance is not only a matter of ensuring that some technical best practices are met but it is also ensuring that what has been architected is what is deployed: that’s where automatic document & diagrams generation comes into play.